1. Introduction
Technological and communication advances, together with the social need for protection and intruder detection, have triggered the massive installation of video surveillance systems in recent years. Due to the large amount of information that is currently captured, stored and transmitted in image, audio and video formats, new cryptography techniques have been presented, and they have received the attention from a scientific and academic community with a view to generating more sophisticated, secure and faster proposals for these format types, since traditional cryptography methods are not effective for this purpose [1,2].
Cryptography schemes that have arisen for image, audio and video formats take advantage of several theories such as elliptic curves [3], DNA sequences [4], quantum computing [5,6], discrete transforms [7,8], chaos theory [1,8-12] and cellular automata [6,11-18].
Connection between cryptography and nonlinear dynamic systems theory has given rise to a line of research called chaotic cryptography, which approaches have been on the rise in recent years [10]. These approaches take advantage of intrinsic properties of continuous and discrete chaotic dynamic systems, that provide inherent strengths in information masking and have proven to be a security alternative for image, audio and video encryption. Nevertheless, reported disadvantages of chaotic cryptography in literature refer to the high computational cost and the required numerical precision of those algorithms to ensure high sensitivity [19].
Cellular Automata (CAs) were introduced in the late 1940’s by von Neumann [20], as a mathematical model with a set of transformation rules that operate on a rectangular mesh formed of a finite number of cells, that interact and evolve in discrete time steps according to a local transition rule and may exhibit complex behaviors. In the last years, CAs have been used in several biological contexts [21,22]. Currently, CAs are an interest technique in the designing of image encryption methods, since it is possible to interpret and treat an image as the initial state of a Layered Cellular Automaton (LCA) and define encryption mechanisms based on its evolution [13,14]. Efficient and robust methods use CAs for image [14-17], audio [18] and video encryption [13]. Several cryptosystems merge CAs with other several approaches such as chaos theory [11,12] and quantum computing [6].
According to the amount of information that is encrypted, two categories of video encryption have emerged: In the first, the frames that constitute the video are fully encrypted [23]; and in the second, only the regions of interest (RoIs) are considered, defined as the frame segments that contain sensitive information [13]. The second category is more efficient since the size of sensitive information is reduced. In [24-27], different methods of detection and extraction of RoIs have been proposed, which consider movement, people's faces, text, among others, as a kind of sensitive information.
In this paper, LCAs and chaos inherent properties are used for the construction of a surveillance video encryption method that uses Composite Cellular Automata (CCAs), one- dimensional CAs designed for this method, which rules are constructed with the reversible elementary rules defined by Wolfram [28]. The proposed encryption method is symmetric and applicable to grayscale and color videos. The sender uses fixed size keys for the encryption of rectangular RoIs defined by motion perceptions in video frames. Encrypted RoIs conserve their original size.
On the other hand, the receiver uses the same keys to recover the original video from the encrypted RoIs and the video frames with hidden RoIs coming from the sender.
This paper is organized as follows. In Section 2, theoretical bases of this work are described. In Section 3, the developed encryption method is described in detail. In Section 4, experimental tests and performance analysis of the implemented cryptosystem are performed. Finally, Section 5 lists the conclusions and contributions of this paper.
2. Theoretical framework
Theoretical principles that support the work presented in this paper relate properties of cryptographic systems to the characteristics of one-dimensional CAs, to contribute in the information security field with a proposal applied on surveillance videos.
2.1. Cryptographic systems
Cryptography arises from the need to ensure confidentiality, integrity and availability of information. Consequently, cryptographic systems are designed and implemented, with the aim of transforming meaningful information into unintelligible data through a hiding mechanism that uses secret cipher keys and allows exclusive access of authorized users to the original information by a decryption process. On the other hand, cryptanalysis seeks to detect vulnerabilities in cryptosystems in order to retrieve or supplant information [29].
There are two types of cryptosystems: symmetric and asymmetric. In symmetric type, the same key is used at both ends of a communication channel, while in asymmetric type each user has a public and a private key [29]. Algorithms based on CAs or chaos that have been proposed for image and video encryption are usually of symmetric type.
In this work, density of periodic points, topological transitivity, and sensitive dependence on initial conditions of the combination of CAs pseudo-random behavior among with additional operations of integer numbers are used to induce the confusion and diffusion properties that should be part of a cryptographic method [30-32].
The confusion property seeks to ensure that the cryptosystem evolution in time is independent of the encrypted text and the cipher key, that is, that the relationship between text and password is sufficiently complex to guarantee security. On the other hand, the diffusion property seeks that small changes in the original text should generate completely different encrypted text [30].
2.2. Cellular Automata
Cellular Automata (CAs) are massively parallel homogeneous discrete dynamic systems [20] with the capability to exhibit complex behaviors. They are represented by an n-dimensional matrix with a finite number of cells, where each cell i has a state s i from a set of possible states S and evolves, synchronously with the other cells of the matrix, in discrete time steps according to a local transition rule or evolution function. The updated state of each cell depends on the entries of this function, which are the previous states of a set called neighborhood, that is conformed of the cell itself and some adjacent [11,33].
The number of possible evolution rules N R for a one-dimensional CA is calculated by using eq. (1), where k is the cardinality of s , and n is the number of cells that compose its neighborhood [21].
Boundaries of CAs can be periodic, reflecting or fixed [22]. Periodic boundaries are used in the proposed method.
Elementary Cellular Automata (ECAs) are one- dimensional, each cell in an ECA has three neighbors and the set of possible states is 𝑆 = {0,1}. According to eq. (1), there are 228=256 different transformation rules for ECAs, called elementary rules, that are identified by integer numbers in the interval from 0 to 255 [28]. The next state for a cell I in an ECA in function of a given elementary rule f is calculated by eq. (2), which is defined in terms of neighboring cells.
Fig. 1 schematizes the evolution of an i th cell in an ECA.
Wolfram [28,33] classified elementary rules into four types according to behavior of CAs in space-time diagrams: homogeneous stable (class I), periodic stable (class II), chaotic (class III) and complex (class IV). Rule 30 is classified as class III and has been used as a pseudo-random number generator [28]. Unpredictable behavior with rule 30 increases when the number of cells is large and odd [34], and when avoiding the use of ECA’s entire rows or columns.
An ECA presents reversibility when it is possible to obtain information about its past states through the current state of its cells, that is, when the state of each cell depends on the previous state of a single cell in the neighborhood [33].
Only six elementary rules achieve reversibility on an ECA [28,33], called reversible elementary rules and listed on Table 1. For convenience, in the proposed encryption method an alternative notation for these rules is used in this paper, with respect to the value that takes each cell in the ECA based on its only predecessor in the neighborhood.
These rules can also be classified into two types: Self-Reversible (SRR) and Non-Self-Reversible Rules (NSRR). SRR are those rules that are reversible with themselves; and NSRR are those that do not achieve this property. ECAs have four NSRR (15, 85, 170 and 240) noted as ‘A’, ‘C’, ‘A̅’ and ‘C̅’; and two SRR (51 and 204), noted as ‘B’ and ‘B̅’.
Reversibility property of CAs is useful in cryptosystems design. In one dimension, this reversibility can be determined, although in the literature it has been shown that this property is undecidable for two or more dimensions [20].
Fig. 2 shows the behavior of an ECA that evolves four times with rule 240 (‘A’), and four times with rule 170 (‘C’) to return to its initial state ‘11100000’.
In CAs context, it is possible to interpret an image I with size 𝑀×𝑁 as a Layered Cellular Automaton (LCA), since it is a matrix with values in the interval from 0 to 255 (black to white), reason why each value can be represented with a byte [13,14]. If I is a grayscale image, the LCA that represents is an 8-layer CA, that is, a matrix of 𝑀×𝑁×8 bits as shown in Fig. 3. If I is a color image, it is possible to represent it by three adjoined 8-layer CAs that form a 24-layer CA.
In the proposed method, each row or column that constitutes any layer in the LCA is considered as the initial state of a one-dimensional CA. The maximum number of one-dimensional CAs that constitutes a LCA obtained from I is given by eq. (3), where the function 𝑚ax(𝑀,𝑁) returns the maximum value between M and N, and the L value is 8 in grayscale images or 24 in color images.
3. Proposed cryptographic method
In the following subsections, the key generation technique, the RoI extraction mechanism and the structure of the proposed cryptographic method are described. The central axis of this method is a kind of reversible one- dimensional CA.
3.1. Composite Cellular Automata definition
The kind of CAs formulated in this paper are named Composite Cellular Automata (CCAs). They are one- dimensional and ECA-based, since their transition rules are a combination of elementary rules. They are called composite rules, with which new possible behaviors emerge that cannot be obtained independently through ECAs.
Formally, a composite rule F is given by expression in eq. (4), where f i is an elementary rule and r is the number of elementary rules that constitute F.
In turn, each f i defines the state for a set of r cells in the CCA from 𝑖 to 𝑖+𝑟−1 through the expressions in eq. (5). The number of bits that represent a composite rule is 8 x r because an elementary rule is identified by eight bits.
Fig. 4 shows a 6-cell periodic boundaries CCA that evolves with a composite rule with r = 2.
Utilization of CCAs has several advantages: a greater number of rules, the possibility of establishing new reversible rules, and an efficiency that resembles ECAs homogeneity.
3.2. Reversible composite rules classification
A reversible CCA evolves with a composite reversible rule, that consists exclusively of elementary reversible rules. The number of cells of a CCA must be multiple of r to ensure that every fi on F is used the same number of times.
For simplicity purposes, alternative notation presented in Table 1 is used to identify any reversible composite rule as a string of r characters, each one has six possible values (‘A’, ‘A̅’, ‘B’, ‘B̅’, ‘C’, ‘C̅’). Nevertheless, not all possible combinations of these values identify a reversible composite rule. In the proposed method, the r value is equal to 8.
In the CCAs environment, new NSRR arise, that involve displacement in the same direction, labeled as Composite Shift Rules (CSR), and formed exclusively of the elementary rules ‘A’ and ‘A̅’, or ‘C’ and ‘C̅’. Fig. 5 shows the behavior of a CCA with initial state ‘11100000’ that evolves four times with rule ‘AAAAAA̅AA’ and other four with rule ‘CCCCC̅CCC’ to return to its initial state.
In addition, reversible rules with capability to change the order of bits of an initial state arise, labeled as Bit Position Change Rules (BPCR). Fig. 6 shows the behavior of a CCA with initial state ‘00101010’ that evolves four times with composite reversible rule ‘BCABCABB’. Note that this BPCR is also an SRR. Nevertheless, there exist NSRR type BPCRs, as in the case of rules ‘BC̅ABC̅ABB’ and ‘BCA̅BCA̅BB’.
Finally, Identity-Complement Rules (ICR) arise, they are composed exclusively of the elementary rules ‘B’ and ‘B̅’, and they are also SRR.
In Fig. 7, reversible composite rule classification performed in this work is shown.
The number of composite reversible rules N CRR for a given r value is calculated using eq. (6)-(9), where N BPCR , N CSR and N ICR represent the number of BPCR, CSR and ICR type rules, respectively.
Note that N CRR grows considerably as the r value increases.
3.3. Composite reversible rules for LCA encryption
From possible composite reversible rules with r value equal to 8, sixteen pairs were selected with the purpose of establish a different 4-bit sequence identifier for each one, they are listed in Table 2. The first eight pairs are CSR, and the eight remaining pairs are BPCR. The rules on the first column (rule set 1) are used in encryption, and the remaining (rule set 2) in decryption, that is, in original information recovery.
As a strategy for the selection of eight first pairs of rules (numbered from 0 to 7 in Table 2), entropy values of the 256 possible 8-bit strings, finding 70 different combinations with entropy value 1, that is, strings which have four zeros and four ones in any order. From this string set, a group of eight was selected with a Hamming distance equal to four or six [35]. With these strings, eight CSR were constructed, first four are composed of ‘A’ and ‘A̅’; and remaining four are composed of ‘C’ and ‘C̅’, being the number 1 replaced by ‘A’ or ‘C’ and the number 0 replaced by ‘A̅’ or ‘C̅’.
Similarly, as a strategy for the selection of rest pairs of rules (numbered from 8 to 15 in Table 2), the set of 15 possible 8-bit strings with exactly two pairs of consecutive ones are considered because their entropy is also 1, and a group of eight with a Hamming distance equal to two, four or six was selected from this set. With these strings, eight BPCR were constructed, being each pair of ones replaced by the elementary rule pair ‘CA’, ‘C̅A’, ‘C̅A̅’ or ‘CA̅’, and each zero is replaced by ‘B’ or ‘B̅’.
3.4. Regions of interest detection and extraction
In the encryption process, the sender stores the original video with hidden RoIs, the isolated cipher RoIs and their location in the video frames. Thus, a receiver can recover the encrypted video completely through the stored data and the correct keys.
The encryption method is tested with a straightforward mechanism for RoI detection, that consider perceptible motion patterns in video as RoIs. An initial frame is considered as background, and the next frames are compared with initial frame to determine the pixels with changed value. If a group of pixels with changed value is connected and has a size greater or equal than 256 pixels, it will be enclosed by a rectangle and considered as a RoI. If two RoIs are 16 pixels away or less, they are grouped into an only RoI. Finally, each RoI dimensions are rounded to the closest multiple of 8 in order to allow a correct encryption process. This process was implemented through a routine in Matlab, using Image Processing Toolbox and Image Acquisition Toolbox libraries.
3.5. Key generation
Starting with an LCA from a predetermined image (such as example in Fig. 3) an initial sequence of 1027 consecutive bits is extracted to form a 1027 columns matrix along with the LCA bits from a RoI, repeating, if required, bits from initial sequence to fill all columns. Subsequently, XOR operation is performed with each column entries, obtaining a 1027-bit sequence that will be the key to encrypt every RoI in a frame.
The first 1023 bits in the key are named Ps0, and the remaining four bits in its decimal representation define the value N 0 that indicates the iteration number to evolve Ps0 with elementary rule 30.
3.6. Cryptographic method steps
The encryption proposal consists of eight steps that are applied on each video frame.
Step 1: RoIs detection, extraction and replacement by black rectangles in the original frame for storage.
Step 2: Transpose RoIs which height is greater than their width.
Step 3: A RoI in the frame is selected for key generation as explained in Section 3.5. RoIs in different frames are encrypted with different keys.
Step 4: Let S ECA be an ECA initial state, and N the number of evolutions with elementary rule 30, the 1023-bit sequence ps is calculated by expression in eq. (10), assigning to S ECA and N the previously defined values of ps0 and N 0 respectively.
Step 5: Bit in position 1024 from the key is appended to ps and read from right to left in 4-bit segments. Decimal representation of each segment is obtained adding one, avoiding the appearing of zeros, forming a list of 256 integer numbers in the interval from 1 to 16 called multiplier sequence ms.
Step 6: Composite rule identifiers sequence R, expressed by eq. (11) is obtained from algorithm 1, assuming that ps and ms have periodic boundary conditions, where Ns, previously specified in eq. (3), is the maximum number of CCAs in the LCA that is obtained with the RoI of the largest width or height in the frame, and Ri is a 4-bit string associated to a composite rule in Table 2.
In this step, rule 30 (eq. 10) is used to evolve ps, that along with multiplication and modulo of integer numbers in ms contribute to guarantee key sensitivity. The values in ms are used in the algorithm 1 to define numbers for the ps evolution with elementary rule 30 and determine the js values that acts as a displacement number for ps. Note that the bits that constitute R are 4-bit sequences coming from a specific ps state.
Step 7: Evolution of LCAs obtained from each RoI. Each row that constitutes the layers in the LCA is considered the initial state of an CCA which corresponding evolution rule is identified by R i . For encryption, the bits that form each LCA are reordered in three different ways:
One evolution is performed after each rearrangement, thus, every LCA evolves three times. For decryption, each LCA evolve before each rearrangement, which order is inverted.
Step 8: Obtain encrypted RoIs from evolved LCAs. Transpose the previously transposed RoIs in Step 2 to recover their initial dimensions.
The sender stores the cipher RoIs, and the receiver decrypt them to completely recover each frame of video. Decryption uses the second rule set in Table 2 to perform the same process except for steps 1 and 3, because the decryption key for original video recovery is the same encryption key.
4. Performance evaluation, analysis and discussion of results
To corroborate the effectiveness of the proposed encryption and decryption process, a series of test and performance measures based on the image encryption literature [1-17] were performed. Each test allows to deduce that the proposed method excels as a security alternative and it is applicable in real environments.
4.1. Experimental tests
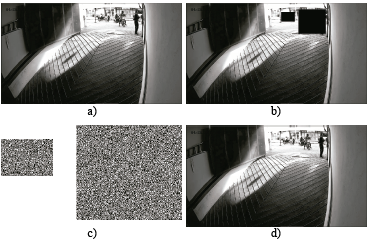
In order to show that proposed method is functional, robust and effective, a surveillance video segment coming from a security camera in the Universidad Distrital Francisco José de Caldas from Bogotá was encrypted. Fig. 8 shows a video frame, RoIs extraction and hiding, encryption and recovery of original image results.
Source: The Authors.
Figure 8 Application of the proposed method in a surveillance video. (a) Original frame, (b) Frame with hidden RoIs, (c) Cipher RoIs, (d) Recovered frame through decryption process.
Executions of this algorithm were performed on a computer with 8GB RAM and processor Intel Core i3 in the Matlab 2018a platform. Encryption and decryption times in for different sizes of image are shown in Table 3.
Proposed algorithm depends on image dimensions, that is, the number of CCAs that evolve in Step 7 and their length. Therefore, its computational complexity is 𝑂(3×𝑀×𝑁).
4.2. Key space analysis
A cipher key in the proposed method is formed by 1027 bits. Thus, the key space size to encrypt a video frame or image is equal to 21027, that is greater that other proposals with same purpose as [1,3,6,8-15], which guarantees resistance to brute force attacks. In addition, it grows proportionally with the number of frames in a video.
The following subsections refer to four images that have been encrypted with the proposed method. Original and cipher images are shown in Fig. 9.

Source: The Authors.
Figure 9 Original and encrypted images. (a) Black image with size 256 x 256, (b) Encrypted black image, (c) Cameraman with size 256 x 256, (d) Encrypted cameraman, (e) Grayscale Lena with size 512 x 512, (f) Encrypted grayscale Lena, (g) Color Lena with size 512 x 512, (h) Encrypted color Lena.
4.3. Histogram analysis
In Fig. 10, histograms of original and cipher images from Fig. 9 are presented, proving that frequency distribution of pixel values in cipher images is uniform as expected.

Source: The Authors.
Figure 10 Histogram of images from Fig. 9. (a) Black image, (b) Encrypted black image, (c) Cameraman, (d) Encrypted cameraman, (e) Grayscale Lena, (f) Encrypted grayscale Lena, (g) Color Lena, (h) Encrypted color Lena.
4.4. Entropy analysis
For a grayscale image I, the entropy H(I) measures the pixel distribution values, which optimal values for a cipher image tends to 8 [13, 30]. It is defined by eq. (12).
Where xi is the i th gray value of I,p(xi) is the occurrence probability of x i and L is the number of pixels that constitute the image. For color images, this conception is applied on each RGB channel. Entropy values of original and cipher images in Fig. 9 are listed in Table 4, proving that encrypted images by proposed method present high randomness.
Obtained entropy values for cipher images are comparable to the values obtained in [1, 3, 5-13, 16, 17]. In addition, entropy value of cameraman cipher image in [13] is 7.988, less than the obtained with this method.
4.5. Differential attack analysis
Let E1 and E2 denote two images which result of encrypt two almost identical images with one-pixel difference, the Number of Pixel Changed Rate (NPCR) is the number of pixels at the same location in E1 and E2 with different values, and it is defined by eq. (13)-(14).
The Unified Averaged Change Intensity (UACI) is the average absolute value of the difference between each pair of pixels at the same location in E1 and and E2, it is defined by eq. (15).
For two random images, NPCR and UACI optimal values are nearly 99.6094% and nearly 33.4635%, respectively [36].
Let I1 denote an image from Fig. 9, I2 equal to I1 except for a modified pixel value. E1 and E2 are the images obtained by encrypt I1 and I2,respectively. Minimum, maximum and average obtained values of NPCR and UACI in 10 executions are presented in Table 5, which are close to the optimal values, proving that the proposed method resists differential attacks.
4.6. Correlation of adjacent pixels
The correlation coefficient for an image is a decimal value between -1 and 1 defined by eq. (16)-(19) and it is calculated from a random adjacent pixel sample in different directions. In plain images, the correlation coefficient is close to 1, and the expected value in cipher images is close to 0 [13].
In order to measure the existent correlation between adjacent pixels in images from Fig. 9(g) and Fig. 9(h), a set of 1000 random pairs of pixels in horizontal, vertical and diagonal position were considered for each RGB channel.
Obtained values are grouped in Table 6, showing an almost null correlation value in every channel of the cipher image.
Fig. 11 shows the horizontal, vertical and diagonal values of adjacent pixels in the green channel for the original and the cipher image.
4.7. Key sensitivity
A feature of secure cryptosystems is key sensitivity, that means, a slight change in the cipher key must produce a completely different cipher result [30].
In order to prove key sensitivity from the sender side, the image from Fig. 9(c) was encrypted using two keys K1 and K2 with one-bit difference, obtaining the results shown in Fig. 12. The UACI and NPCR values related to the images in Fig. 12 (b) and (c) are 99.61% and 33.42% respectively, that implies that these cipher images are completely different.

Source: The Authors.
Figure 12 Encryption of image with two similar keys. (a) Original image, (b) Encrypted image using K1, (c) Encrypted image using K2.
In order to prove key sensitivity from the receiver side, K1 are K2 are used to decrypt the image from Fig. 12(b), obtaining the results shown in Fig. 13.

Source: The Authors.
Figure 13 Decryption of a cipher image with two similar keys. (a) Cipher image, (b) Decrypted image using K1, (c) Decrypted image using K2.
Note that original image is completely recovered by using K1, but it is not possible to retrieve encrypted information by using K2
It is remarked that every sensitivity test shows similar results, independently of the position occupied by the difference bit between K 1 and K 2 . Therefore, this method presents key sensitivity.
The results presented in this section expose that the proposed method resists brute force attacks, correlation attacks, differential attacks, chosen-plaintext attacks according to performance results in encryption of Fig. 9(a), and known-plaintext attacks as an effect of the strategy in Section 3.3, which frustrates the possibility of obtain the rules in R without having the cipher key.
Although there are few encryption works focused on surveillance videos using the guideline proposed in this work, it was possible to calculate a collection of performance measures reported independently in several references, highlighting that the obtained measures are comparable with those in [1,3,5-13,15-17]. That implies high security of the proposed method and makes this work a significant contribution in the fields of image and video encryption.
5. Conclusions and future work
The implemented CCA-based encryption method presents quantitative and qualitative optimal performance values, demonstrating that is an effective security alternative. Nevertheless, the efficiency of this method is dependent on the size of the RoIs.
The proposed method is extensible and modifiable since not only a high number of composite reversible rules can be applied to the cryptosystem, but also it is possible to increase or reduce key size because it is not dependent on the size of the RoIs.
Rectangular shape of RoIs could be adjusted to irregular contours with the aim of increase encryption efficiency. In addition, it is possible to modify the RoIs detection and extraction mechanism to avoid equivocal motion perceptions such as shadows reflected by lighting.
Combining the behavior of elementary rule 30 with the multiplication and modulo operations to random numbers in the developed algorithm increases randomness and sensitivity of results in the proposed method, that implies the impossibility of successful fraudulent attacks.
















































