I. INTRODUCTION
Recent studies show that the use of smartphones in Colombia continues to rise. Currently, 96% Colombians use a mobile phone in their daily life [1], most of them are used to store personal information such as photos, videos, bank accounts, and confidential documents of their companies [2]. Incidents related to information theft from mobile devices affecting ordinary citizens decreased by 35% between 2014 and 2016, while attacks to businesses had an increase of more than 20% [3]. This affects many people and has consequences on a psychological, physical, and financial level. One of the most vulnerable groups are university students, who store personal information and conduct transactions in their mobile devices using free and insecure public networks [4]. This article presents an investigation with students from various universities in the southwest of Colombia to identify the risk their mobile devices are exposed to.
GDroid [6] is a tool to detect malware or vulnerabilities in Android, to do so, it uses convolutional neural networks (CNN) to map Android APIs and applications into a heterogeneous graph, then a node classification task is carried out based on the invocations to the Android API and the Usage Patterns. TC-Droid [7] presents a framework that feeds on the text sequence of the application reports generated by AndroPyTool and applies CNN to explore them. In [8], a CCN-based malware detection model that uses an Android application's operation code sequence is presented, to do so, Dreblin´s dataset is used [9].
DCDroid [10] offers a tool to detect vulnerabilities by combining static and dynamic analysis. In the static analysis, it focuses on identifying several types of vulnerabilities in application code snippets. In the dynamic analysis, it prioritizes activation of user interface (UI) components based on static analysis results to confirm SSL / TLS misuse.
As can be seen in the related works, existing approaches are based on neural network models with very good results in the classification of malware; however, none of them study the behavior of real users directly to identify the most frequent vulnerabilities.
The remainder of this article is organized as follows: Section II presents the case study and the mobile application developed; Section III exposes the results; and Section IV presents the conclusions and future work.
II. CASE STUDY
The case study is descriptive/holistic, and it is based on Runeson’s methodology (Figure 1) [11]. The main objective is to identify the vulnerability of mobile devices with the Android operating system used by university students from the southwest of Colombia.
A. Selection of the Study Population
The population is made up of university students between 16 - 25 years old because of their vulnerability; many times, they do not have precaution when connecting to free Wi-Fi networks or providing information, thus leading to information or credentials theft. The students use a smartphone with Android operating system. The population consists of 129 participants and is described in Figure 2.
B. Compliance with Restrictions
Information about Android vulnerabilities from version 5.0 to 10.0 is collected from the National Vulnerability Database (NVD) provided by the National Institute of Standards and Technology [12].
C. Initial Meeting
Vulnerabilities, severity, and details are classified using the analyzed data. On August 28 and 29, 2020, two meetings were held via Zoom: one meeting with 70 people and another with 59 for a total of 129 students from different universities.
D. Evaluation with the App
The analysis unit corresponds to the execution of the process, that is, the installation of the application on the devices by a cybersecurity expert, thus measuring qualitative and quantitative aspects. At a quantitative level, the vulnerability identification time was considered, and for the qualitative aspect, through the evaluation of the expert, it was determined to what degree the devices are vulnerable. Table 1 shows the results of the versions found and the app installation messages.
Table 1 Android Versions.
| Version | Number of devices | Message during installing |
|---|---|---|
| ANDROID 5 | 10 | Message configuration during installation |
| ANDROID 7 | 15 | Automatically installed |
| ANDROID 8 | 40 | Confirmation Message during installation |
| ANDROID 9 | 30 | Message configuration during installation |
| ANDROID 10 | 34 | Message configuration during installation |
| TOTAL | 129 |
E. Application of Validation Instruments
Surveys were used as information collection methods. Two vulnerability identification cycles were defined to establish how the repetition of the execution process affects the results obtained. At the end of the two cycles, it was decided to conduct a survey to each participating student about the process and implementation of the application.
F. Mobile Application
To conduct the case study, it was necessary to develop an application named Android Protect. It has the functionality of identifying whether there are vulnerabilities in the mobile device it was installed to, then each of its components is shown.
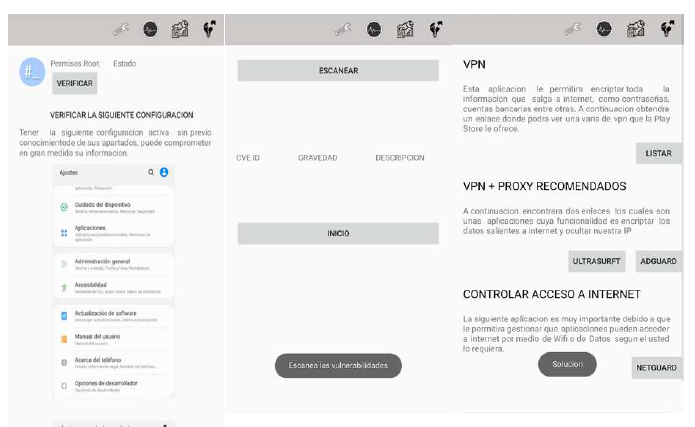
Figure 4 shows the application toolbar which illustrates the icons of each module. The first icon from left to right is a key, which represents the configuration module; the second is a circle and it is one of the most important because it scans the vulnerabilities according to the version used in the mobile device; the third icon shows sheets and graphs, it is the results module that shows the terms related to the configurations and scans of the vulnerabilities in a clear way and with a brief description, in addition to the most common attack; finally, the fourth icon is a light bulb, which provides some alternatives as a solution to counteract data leaks. In addition, the sources from which the registered vulnerabilities are extracted in real time according to the version of each device are detailed with a brief description of each menu. In module 1, when entering the application, it asks the user for permissions, which are shown below.
The first module of the application verifies if the mobile device is with Root access, that is, released with all the permissions to use the device. Module 2 is the most important as it generates the device's scanner, it has a table of 3 items which categorizes the scanned information for a better understanding, this is done in technical terms which help to know the severity, the description of the vulnerability, and the code of the vulnerability. The scanning process is done using the Web Scraping technique, which consists of capturing the vulnerabilities registered by the manufacturers in a table according to the Android version of the device, then the application shows the results of the scan. Module 3 displays the vulnerabilities.
Module 3 shows the most frequent attack techniques on mobile devices, it also describes the configurations presented in module 1 and informs why these configuration options should be disabled (e.g., keep the device without Root access). Moreover, there is a brief description of the module. Finally, Module 4 shows the recommendations of tools and actions that help to take care of the device such as:
VPN maintains control of the internet connection and modifies the geolocation to make an anonymous bridge of the data managed by the device, on the other hand, it allows to encrypt the susceptible information on the internet.
VPN + PROXY: This service allows the user to encrypt the outgoing data to the internet and hide the user's IP, using Ultrasurft [13] and Adguard [14].
CONTROL OF INTERNET ACCESS: Here Netguart is used to control the entry and exit of data to the network, it has a firewall that allows controlling the internet access of each application installed on the mobile device, providing better control of the data flow [15].
III. RESULTS
The evaluation of the case study was conducted with 129 students from different universities in the southwest of Colombia, the installation of the Android Protect application was carried out on the different devices used by the participants, from Android 5.0 Lollipop up to Android 10.0. The scan was successfully performed on those versions and their derivatives. After that, a laboratory where the devices were infected with spyware and persistent backdoor [16] was developed. The practice consisted of verifying the effectiveness of the Android Protect to stop the viruses. Other sections such as Root access detection and configuration enabled in developer mode were also evaluated.
Figures 5 and 6 show that 19% of the devices were detected by Google Play Protect, since it is responsible for blocking the installation of malicious applications on their device. The 12% allowed the installation without any protection, and 70% display a message requesting for permission to install it. The 19% of the devices had Root access, allowing them to view any type of data and to modify it, 81% of the devices did not have Root access.
On the other hand, it was observed that 22% of devices had disabled Google Play Protect (The device is pre-configured to accept external applications); 78% have Android protection enabled, so it does not allow applications to be installed automatically. Finally, it is evident that 100% of the devices in the laboratory are vulnerable because none have a stable protection that allows them to prevent the installation of applications or malicious elements.
V. CONCLUSIONS AND FUTURE WORK
The case study shows the importance of being aware of security issues in our mobile devices; it is recommended to consider these issues to improve self-care.
A mobile application with four modules was developed to help users to verify the security of the mobile device: First, an analysis of the internal configuration (Root access, debugging mode); Second, scanning vulnerabilities; Third, the most common vulnerabilities are explained; Finally, a section about how to prevent the vulnerabilities.
It is also concluded that 100% of the devices were vulnerable because they had a malicious software blocker; however, it was not enough to prevent malicious installations. Many devices had a wrong permission assigned by the owner; therefore, it is recommended to be informed on the subject and in this way avoid these problems.