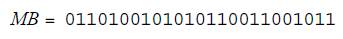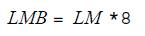Introduction
Currently, drones have acquired great importance, since they allow us to reach difficult-to-access areas remotely. Therefore, the Mexican Ministry of Communications and Transportation has indicated they should only be employed during daytime hours in areas not classified as prohibited, restricted, or dangerous (SCT, 2015). Drones are an excellent tool used in security matters regarding different types of transport (Reshma, Ramesh, & Kumar, 2015). However, drones possess vulnerabilities, such as those found in a security analysis where it was determined that an attacker can have access to them and obtain information due to the management of control commands, telemetry, data, and video via Wireless Local Area Networks (WLAN) without any type of encryption (Samland, Fruth, Hildebrandt, & Dittman, 2012). Thus, it is necessary to implement security measures, with the cryptography focused in the encryption of data not to be interpreted, or with the steganography specialized in data concealment (Morocho-Checa, Zambrano-Miranda, Carvajal-Rodríguez, & Lopez-Fonseca, 2015). There are systems that take advantage of the information technologies to apply steganography in computing systems (Morocho-Checa, Zambrano-Miranda, Carvajal-Rodríguez, & Lopez-Fonseca, 2015; Rodríguez-Mendoza, 2016). In addition, secret messages can be embedded inside different multimedia containers, exploiting their intrinsic properties, such as spaces in text documents, pixels in images, and frames in videos (Méndez-Naranjo, 2015; Morocho-Checa, Zambrano-Miranda, Carvajal-Rodríguez, & Lopez-Fonseca, 2015; Rodríguez-Mendoza, 2016). Steganography was applied to cloak a message inside a picture, where the pixels are modified according to the Least Significant Bit (LSB) placed along the edges of the image (Ratnakirti, Anirban, & Suvamoy, 2013). Anees et al. proposed a technique to apply digital steganography in which the authors replaced two different areas of an image according to LSB and Most Significant Bits (MSB) (Anees, Siddiqui, Ahmed, & Hussain, 2014). Ranjith-Kumar et al. (2016) proposed a technique to modify LSB and Intermediate Significant Bits (ISB), which enhances the quantity of positions that can be altered by applying steganography; in addition, these authors implemented the technique of confusion in the plain text prior to inserting it into the container. Martínez-González et al. designed a system where they take the plain text and divide it into four bit sections for insertion into the four LSB of an image (Martínez-González, Díaz-Méndez, Palacio-Luengas, López-Hernández, & Vázquez-Medina, 2016). Methods for encoding data have been developed through implementing chaotic systems, due to their desired properties, such as sensitivity to the initial conditions and parameters, rendering them efficient for the design of security applications due to their versatility and complex evolution. In telecommunications, packages with chaotic encryption of poor analytical rigor were sent with satisfying results (Jiménez-Rodríguez, González-Novoa, Estrada-Gutiérrez, Acosta-Lua, & Flores-Siordia, 2016). A security and authentication scheme was developed via a secret 128-bit key, employing a tent map (Sen-Te & Samsudin, 2017). Kanso and Ghebleh (2017) implemented an algorithm with the Arnold's cat map, altering the frequency of the image instead of its pixels; the changes are notable in color images, limiting its use for blacks and whites. A transmission method for combining Electro Cardio Graphy (ECG) signals obtained from a patient with chaotic algorithms was proposed (Bárbara-Morales, Alba-Blanco, & Rodríguez-Ramírez, 2012). Nassar et al. (2016) implemented a scheme where encryption and steganography are applied, utilizing the Logistic map for encryption and noise conversion and the Baker map for steganography. Sharif et al., designed a system in which chaotic maps are implemented to generate three positions plus dividing the byte-to-insert into four bits, which are embedded in the container, replacing the four LSB of two positions (Sharif, Mollaeefar, & Nazari, 2016). A scheme consisting of the insertion of a message into a container was proposed; the resulting stego-image is encrypted and inserted into another container afterward (Baig, Khan, Beg, Shah, & Saleem, 2016). Xiang et al., developed an algorithm in which each character of the message is divided into two, four-bit sections, where the MSB and LSB are placed in two positions generated by the chaotic system, replacing its four LSB. This algorithm is designed to work with black-and-white pictures and a message shorter in size than that of the container image (Xiang, Hu, & Sun, 2015). Ghebleh and Kanso apply criteria to generate values between 5 and 250 and to focus on edge detection within a container image, where they hide information in the frequency domain (Ghebleh & Kanso, 2014). Aziz et al., designed a system consisting of two phases: in the first, the message-to-conceal is encrypted as noise, and in the second, the resulting cryptogram is embedded in the container image. The selected byte is divided into three-bit segments to be inserted into the LSB of a pixel. This is designed to work with images of 256 colors or grayscales (Aziz, Tayarami-N, & Afsar, 2015).
Drones are widely used, because they allow video recording and taking pictures of places where access is difficult for persons. However, there can be malicious users remotely connected to the drone who intend to take possession of the photos or videos recorded by it. Thus, it is necessary to implement measurements that permit origin claim; in this manner, it could be determined from which device the images were captured. With that goal in mind, this paper implemented a system connected to a drone and applying a novel steganography technique to identify the device employing chaos. It is focused on the LSB scheme, but only modifies it a little, differentiating it from systems in which three or four are replaced (Aziz, Tayarami-N, & Afsar, 2015; Martínez-González, Díaz-Méndez, Palacio-Luengas, López-Hernández, & Vázquez-Medina, 2016; Xiang, Hu, & Sun, 2015). The aim of this research is the development of a system capable of hiding an identifier in a manner imperceptible to the human eye in the photographs captured from a drone, to safeguard the copyright of the owner of the device, implementing a steganography technique that selects in chaotic way the RGB colors of the image and modifies only the least significant bit of the selected channel. The algorithm was developed in Java, so it is completely portable and can be executed in multiple platforms of operating systems or in single board computers that adapt to the drones with insufficient processing capacity. The steganography method can be used in different research areas to hide information in containers such as: images, videos, bio-signals, data and audio, among others. The remainder of this article is organized as follows: in the methodology explaining the process to apply steganography in images is displayed, in discussion and results analysis section, made different tests to verify the security of the system is exhibited, in conclusions we obtained are detailed.
Methodology
For follow-up, the mathematical model used for the system tests is explained. It is important to highlight that any other chaotic model can be implemented.
Chaotic system: Rõssler oscillator
In 1976, Otto E. Rõssler found a relatively simple system that possesses an elemental geometric building of chaos in continuous systems and that is represented by the set of following Equations (1a) to (1c).
The equation system is composed of three initial conditions (x0,y0,z0) and three control parameters (a,b,c), which are utilized as encryption keys (Rõssler, 1976).
System operation
The system can hide any type of data inside images that are composed for pixels, and these, in turn for subpixels (RGB), which have values between 0 and 255.
To conceal information, the Rõssler oscillator is employed to generate three chaotic orbits, according to their variables (x,y,z), from which one is utilized to select the pixel of the image, another, the subpixel (RGB) and, in case of applying steganography in video, the latter is used to choose a random photogram.
Here below, the steps are explained for using the Rõssler oscillator:
Capture the image from the drone, which will serve as our container file to hide its identifier.
Store the identification in a file.
Convert the identification into binary code.
Implement the proposed algorithm to conceal the identification in the container file.
Create the stego-image.
This process is illustrated in Figure 1.
Following this, the process to embed the identification inside an image is explained, although any type of information in bit format can be inserted as well.
Nomenclature
IC: Original or container image where the message will be randomly hidden.
M: Message or identifier to be sent as concealed within the container.
Ste: Image after the message has been inserted (stego-image).
Encryption keys:
x0,y0,z0: values assigned to the initial conditions.
a,b,c: values of the control parameters.
Algorithm 1: Stego-image generator
Step 1. Store in variable LM the characters contained in message M.
Step 2. Convert LM characters, blank spaces, symbols, letters, numbers, into their respective binary value (0 and 1) and store them in MB.
Step 3. Determine the length of MB, which would be equal to multiplying the length of the LM message times 8 (corresponding to the number of bits for each character) and assign it to LMB.
Step 4. Calculate the number of pixels stored in image IC, to determine the length of the vectors in which they will be saved afterward (multiplying the width by height of the image).
Step 5. Assign the values of each corresponding RGB pixel of image IC, in their respective vector.
Step 6. Solve the system of Equations (1a) to (1c) with the keys (initial conditions and parameters), to generate 3 vectors where the chaotic orbits x, y, z, are stored, this step is repeated until a vector of length L_IC is generated.
Step 7. Take a term of x to divide it between the absolute value of the largest number of the vector x, in order to generate a float between 0 and 1. The result is stored variable norm.
Step 8. Calculate location loc multiplying L_IC by norm. Afterward, the result is rounded off and its absolute value is taken. Therefore, a position between 0 and L_IC will be generated.
Step 9. Determine the RGB color channel to modify, taking a value of y, generated in step 6. It is divided by the largest number of its vector and multiplied by 2; afterward, it is rounded off and the absolute value, obtaining a number indicating the RGB vector that will be altered, which can be one of the following: 0 modifies vred, 1 alters vgreen or 2 vblue.
Step 10. Verify whether color equals:
0, take value val stored in position pos of the array vred[pos].
1, take value val stored in position pos of the array vgreen[pos].
2, take value val stored in position pos of the array vblue [pos].
As shown in the example in Figure 4.
Step 11. Verify that the array and position selected in Step 10 have not been modified previously; otherwise, repeat Steps 7-10.
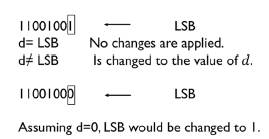
Step 12. Modify the Least Significant Bit (LSB).
If d equals the LSB of val, it remains as it is;
Otherwise, change LSB (if its 0 is replaced by 1; on the other hand, if it is 1, it is changed to 0).
As shown in the example in Figure 5.
Source: Authors
Figure 5 Evaluation to determine whether the Least Significant Bit (LSB) requires modification.
Step 13. Convert val back to decimal and store it in the vector position from which it was taken in Step 10.
Step 14. Repeat Steps 7 to 13 until MB has been concealed in its whole length IC.
On concluding the previously mentioned 14 Steps, stego-image Ste is generated.
Algorithm 2: Recovering the information hidden in the stego-image
For recovery, it is necessary to have stego-image Ste, the cipher keys (parameters and initial conditions used in Step 6 of Algorithm 1), and length of message LMB generated in Step 3 of Algorithm 1.
Step 1. Calculate the number of pixels stored in stego-image Ste.
Step 2. Repeat Steps 5-11 of Algorithm 1.
Step 3. Convert val to binary: val = 200 = 11001000.
Take the LSB of val and concatenate to the end of string MB, as shown in Figure 6.
Step 4. Repeat Steps 2 and 3 until MB is of a length equal to LMB.
Step 5. Group MB in blocks of 8 bits. Each byte is then converted into its respective ASCII value; thus, hidden message M is recovered.
Discussion and Results Analysis
The algorithm was implemented in Java, a multiplatform programming language that allows its execution in any system compatible with the drone or in mobile or desktop applications. We promptly displayed the results obtained in the system from a picture captured by an AR.Drone 2.0, where 1 819 characters were hidden. In Figure 7(a), the original image is displayed, the stego-image is exhibited in Figure 7(b) and, as can be observed, the subpixels in three colors of the stego-image in Figure 7(b) were modified, this imperceptible to the human eye.

Source: Authors
Figure 7 (a) Original image, (b) Stego-image, and (c) Modified pixels in Stego-mage.
In Figure 7(c), the pixels were the LSB in the modified stego-image are shown, marked with red, green, and blue dots depending on the altered RGB channel. The remainder are displayed in black.
Speed
Tests were performed using the system to conceal messages of different sizes within a 640 χ 360 pixel image, captured by the AR.Drone 2.0. The results are portrayed in Table 1. In the column size of the message, the number of characters is indicated that are hidden in the stego-image. In the second, the time taken by the algorithm to hide the data is exhibited, while in the third, the time it took to recover the message from the stego-image is displayed. In the very last, we find the percentage of subpixels altered in the container image.
Statistical analysis
Correlation analysis
To verify the difference between pixels of the container image and of the stego-image, the diagram exhibited in Figure 8 was developed. In this diagram, correlation coefficient value R = 1 can be observed; therefore, the alterations of the stego-image are practically imperceptible, given that the modifications were quite small due to changing only one bit.
Another correlation analysis was developed comparing the data recovered from stego-image with the original message hidden within it, to verify whether the data was recovered completely or whether there was some loss in the tracing. The diagram is shown in Figure 9. The resulting correlation coefficient is R = 1; therefore, there was no data loss at the time that the message was recovered.
The correlation diagram of Figure 10 was performed to verify the sensitivity of the keys used in the algorithm by the Rõssler oscillator to hide the information. In the diagram, the relation between the original message hidden with key values: x0 = 3,451458, y0 = 1,952658, z0 = 7,871425, a = 0,2, b = 0,2, c = 9,5 and the recovered message with the following values: x0 = 3,451458, y0 = 1,952658, z0 = 7,871425, a = 0,1, b = 0,1, c = 9,2 as displayed in the correlation coefficient R = -0,00546, indicating that the relation between the hidden message and the recovered one is practically null, this sustaining the security and confidentiality of the information. Thus, if an attacker intercepts the stego-image, the correct keys are necessary to recover the message.
Histograms
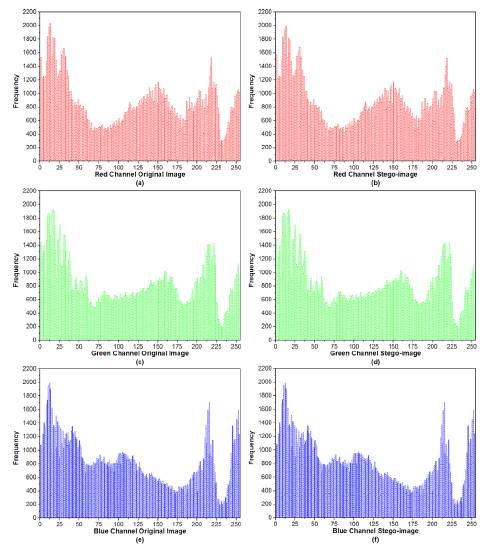
In Figure 11, histograms graphically representing the pixel distribution of the original image and of the stego-image are displayed.
Source: Authors
Figure 11 Histograms of the original image. (a), (c), (e), red, green and blue subpixels, respectively. Histograms of the stego-image (b) red, (d) green, and (f) blue.
Figures 11(a), (c) and (e) present the histograms corresponding to the original image of red, green and blue colors, respectively. In Figures 11(b), (d) and (f), the histograms of the stego-image are exhibited.
Comparing the histogram color pairs, significant changes are not noticeable, this due to the altering of a single bit (the LSB). Ergo, subpixel values in positions randomly chosen by the orbit are only added to or subtracted from 1, but only if this is necessary, therefore rendering the alterations of the image very slight.
Stego-analysis
To detect the small differences between the steganogram and the original image, the statistical security analyzes shown by Anees, Siddiqui, Ahmed, & Hussain (2014) is performed to determine the correlation (Corr), contrast (C), energy (E) and homogeneity (Hom). The correlation of an image is given by:
The contrast of an image is given by:
The energy of a digital image defined as:
The homogeneity analysis processes can be determined by:
To compare the proposed system with other authors, a message is hidden in the image of Baboom Figure 12 (a) and a steganogram is generated Figure 12 (b).
Table 2 shows the results of the statistical analysis applied to Figures 12 (a) and 12 (b), and they are compared with the data of other authors in which they apply the methods Equations (2) to (5) to the same image, in the results it is observed that the technique proposed by Sharif, Mollaeefar, & Nazari (2016) like ours does not present alterations between the original image and the steganogram. Unlike the slight changes generated by the method of Anees, Siddiqui, Ahmed, & Hussain (2014).
Other types of analysis are implemented, such as MSE, PSNR and SSIM (Index quality).
Where Mean Squared Error (MSE), it can be defined as:
The Pick Signal to Noise Ratio (PSNR), it is given as:
The Structural Similarity (SSIM) quality Index is defined as:
Table 3 presents the MSE values calculated by Equation (6) and PSNR with Equation (7) of Figures 12 (a) and 12 (b), the results are compared with Anees, Siddiqui, Ahmed, & Hussain (2014). There, it is observed that our method presents a higher PSNR, indicating better quality in the image, on the other hand the MSE is lower therefore few differences were detected.
The quality index and PSNR are calculated by Equations (7) and (8) with Baboon images of (256 x 256) and (512 x 512), the results are shown in Tables 4 and 5, in which it can observed that the proposed system displays better results.
The results of the statistical analyzes of contrast, correlation, energy, homogeneity, MSE, PSNR and quality index presented in Tables 2-5 were generated in Matlab software.
Conclusions
The proposed system to conceal information within pictures taken by an unmanned aerial vehicle to identity from which device they were taken was implemented in an AR.Drone 2.0; it should be noted that the latter can be utilized in devices without the necessary resources by adding additional hardware or an embedded system to capture, process, and apply steganography in the image. The system guarantees the reliability of exploiting the properties of chaotic mathematic models, such as high sensitivity to the parameters and to the initial condition, employed as cipher keys to hide the message. Thus, only users with access to these can recover the message. Further, it was designed to use any mathematic model and not a specific one; ergo, it can implement any chaos-generating model with the sole requirement of generating two orbits for applying steganography in images and three for video. Additionally, the system fortifies the security by only altering a single bit at a time within the container (the least significant of these, the LSB) and only when it is different from the bit-to-hide. The previously mentioned information makes the modification of the images lessen, and it is more difficult to perceive the changes between the original image and the stego-image; this was tested in the statistical analysis evaluating frequency, the correlation, contrast, energy, homogeneity, MSE, PSNR, and quality index of the images. The system hides the message in the three RGB channels by inflicting chaos inside the whole image; not just the edges; this guarantees the concealment of bigger data and increases the difficulty for an attacking cryptanalysis. The system assures to the 100% integrity of the hidden message checked through the correlation diagrams, where the original message and the recovered message from the stego-image were compared. Therefore, high sensitivity to the cipher keys was verified with another diagram, evaluating the lineal association between the original message and the recovered message with different keys. The proposed system can be used in different research areas that entail working with images, such as Medicine, Radiology, Photogeology, among others.