I. INTRODUCTION
Cyber-attacks are a growing trend in modern Colombian society. These attacks impact users with information on the Internet [1] because the information traffic generated when files are moved from a computer or cell phone to the Internet, always creates an encryption that allows hiding information frames and packages necessary between the modem and the sending device. For this reason, it is necessary to know how such information packages, which contain important information for the security of our data, are attacked.
A. What is WPA2-PSK?
Among the existent wireless networks that allow interconnecting two or more computers to transmit data, the best known are WPAN (Wireless Personal Area Network), WLAN (Wireless Local Area Network), WMAN (Wireless Metropolitan Network), and WWAN (Wireless Wide Area Network). Each network has an associated protocol and IEEE standard that allow the review and the subsequent communication in a local or global network. We will focus on the WLAN wireless network with WPA2-PSK protocol based on the IEEE 802.11i standard that was released on July 24, 2014 [3-5].
WPA (Wireless Protected Access) originated in the problems detected in the WEP, a previous security system created for wireless networks [6]. WPA2-PSK (PSK acronym for Pre-Shared Key) is the evolution of the WPA protocol; it implements an algorithm based on a key of 8 to 63 characters, which is taken as a parameter, and with this value, a new key is randomly generated [6].
The operation of WPA2-PSK involves the following steps (Fig. 1):
The authenticator sends a message to the supplicant with a value generated randomly using its PSK key (an arbitrary value with no special meaning). This message is known as an authenticated nonce or simply nonce, because it contains a field called nonce whose value is generated randomly with the PSK key of the authenticator, as shown in Fig. 1, which was captured with Wireshark. In addition, the Replay Counter is an indicator that allows the authenticator and the supplicant to know the number of packages that have been previously sent [6].
The supplicant receives the message and generates another message called snonce (supplicant nonce), which is basically of the same type as the received anonce package, but contains a different nonce (an arbitrary text generated randomly using the PSK key of the supplicant) [6].
With the previous information, the supplicant creates the Pairwise Transient Key (PTK); this step is extremely important and, therefore, the reader should pay more attention, because is where the "magic" of PSK and the dynamic generation of keys take place, which was implemented in the beginning to improve the security of WEP against fairly widespread attacks. PTK are the keys generated in each packet exchanged between the supplicant and the authenticator, and are generated using the Pairwise Master Key (PMK), but they are the same PSK code generated in step 1; that is, each PTK is generated dynamically by the supplicant PSK and the authenticator [6].
The procedure for generating the PTK key is really important, hence, its understanding is necessary. The PTK is generated by the PMK using a PTK random key generation function that takes the following parameters: 1) anonce, which is the package generated by the authenticator that contains a random text encrypted with its PSK key; 2) snonce, which is the package generated by the supplicant that contains a random text encrypted with its PSK key; 3) MAC authenticator; and 4) MAC supplicant [6].
The supplicant sends a packet to the authenticator with the snonce message and a MIC field (field encrypted using the Michael encryption mechanism) that allow performing an integral and consistent check of the packet; this field is generated by the supplicant using the PTK and the PMK [6].
With the package sent by the supplicant in step 5, the authenticator derives the PTK key, since it already knows the fields necessary to do the calculation: PMK, which is the same for both the supplicant and the authenticator, anonce, snonce, and the MAC addresses of the authenticator and the supplicant [6].
Once the authenticator has generated the PTK with the fields received from the previous packet (with the snonce field), it tries to generate the MIC field, since it has the same PTK and PSK as the supplicant. The MIC generated by the authenticator and the supplicant must be the same, and if that is the case, the authenticator sends a message to the supplicant of the type "Key Installation"; this message can be seen with the "Flag" of the type "Install Flag", which in turn can be seen in the third package exchanged in the authentication process [6].
The supplicant sends to the authenticator a "Key Install Acknowledgment" message, which simply confirms that, in this session of package exchange, the same PTK generated in the client and the AP were used. This package contains a "Key ACK" field with a value of zero, indicating that it is the last message sent in the authentication process between the supplicant and the authenticator [6].
Once the function of the WPA2-PSK protocol is understood, we can perform different types of attacks to detect its vulnerabilities.
B. Types of attack
Modems that create wireless networks for their users are vulnerable to several types of attack. The most common attacks are the following:
SYN saturation attack: flood network traffic. In other words, a single individual makes a large number of requests to the server, in this case the modem, which denies access to the rest of its users [7].
DoS attack: It is a denial of service attack [8].
DDoS attack: it is an extension of the DoS attack, but it attacks from different connection points [8].
Identity theft: Phishing is based on social engineering that focuses on the fact that humans make the greatest errors [8].
Attack by intermediary: It diverts packet information by changing it and returning altered information, or just checking what information is being handled by the target user [8].
II. METHODOLOGY
A. Software
WIFISLAX. Operating system based on Linux that can be used as a live cd or boot access on a USB; it was designed by www.seguridadwireless.net, and was adapted for Wireless [9]. This OS is an audit tool for wireless networks that contains a set of tools to function.
Linset. Application to audit wireless networks that does not use decryption dictionaries to obtain the access code to the network. With this tool, the cooperation of the user, who is unaware of the attack, is of vital importance, which implies that the user has little or no knowledge of computer security. Linset creates a fake AP with the same ESSID, as the one we are attacking and without any type of encryption; in addition, it authenticates the APs of the legitimate clients, preventing them to authenticate, and making them access the AP created by this tool and enter the password of the network [10].
Operation. This tool attack the modem, allowing network users to connect, and then, creating a fake network to which users will connect and provide the network password. Once the password is obtained, the fake network is closed and the modem operation is released.
Aircrack-ng. Complete suite of tools that audit wireless Wi-Fi networks. This tool focuses on different areas of security in wireless networks: packet-monitoring, attack, testing, and cracking [11].
VMware Workstation PRO (trial version). This tool is one of the industry standard products to run multiple operating systems as virtual machines on a single PC. Thousands of IT professionals, developers, and businesses use Workstation Pro and Workstation Player to improve agility, productivity, and security [12].
Windows 8 Pro (trial version). New operating system created by Microsoft. In this case, we will use Windows pro test version for the development of this research.
B. Hardware
Modem ZTE ZXV10 W300E (for home network use)
Desktop computer corei7 16 RAM
Network adapter TP-LINK WN725 (Does not support monitoring)
Network adapter TP-LINK WN722N (Supports packet monitoring)
C. Methods
The modem was configured to generate a wireless network called Security, use the WPA2-PSK protocol, and generate the password for accessing the newly created network. In this case, the network was called Prueba Articulo, and the password was @Prueba@.
We performed the audit using attack by intermediary and DoS attack (for using decryption dictionaries known as brute force), and run ten tests for each technique.
First, we carried out a brute-force attack, that is, an information package was captured with the wireless network encrypted access key. Afterwards, we carried out an impersonation attack, in which a third network that impersonates the original network is created, while the victim sends the password of his/her wireless network. In both attacks, we evaluated anonymity and waiting time to obtain access.
III. RESULTS
This study allowed us to understand better the use of the audit tools. The focus of our analyses was to highlight the vulnerabilities of the security protocol; for this, we studied the following items: time to obtain the password, method, and visualization of the attack (Table 1).
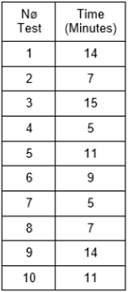
Table 2 shows the length (hours) of each of the 10 tests conducted with the Aircrack tool; whereas Table 3 shows the length (minutes) of the attacks with the Linset tool.
The network attack using Linset was one of the most effective; however, this is not because of the results, but because of the lack of defense methods. Therefore, as long as the attacker has a good network card, the attack is imminent and difficult to avoid if the user is unaware of it.
IV. DISCUSSION
Although companies in Colombia like Digiware are dedicated to computer security, no system is 100 % safe. What is really important for an adequate protection of our data is education; however, how do we obtain this knowledge? Are the supplier companies willing to give us basic training to at least change the password of our wireless network? The truth is that the knowledge we have today is quickly becoming obsolete, particularly in technology; what before lasted a little over a year, nowadays only last for weeks or sometimes days. In the current information age, it is necessary to have a minimum of security in our data, which is why a question arises: who will train us for this?
This article presents two tools to evaluate the security of our wireless networks, and the way the WPA2 security protocol works. Additionally, we provided elementary knowledge about the different types of attacks that currently affect wireless networks. Evidently, besides computer viruses, the attacks to the network infrastructure are problematic because they allow access to the users' sensitive data.
V. CONCLUSIONS
Linset employs more advanced techniques than Aircrack, seeking the ingenuousness of the user to appropriate the networks password. It also uses a technique of alternative creation of networks contrary to Aircrack, which collects identification packages; in terms of time, Aircrack method is more expensive than Linset. Aircrack attacks on vulnerable networks are totally unavoidable, therefore, it would be necessary to find a solution. The delay time that the Linset tool has against Aircrack is limited with respect to time: A Linset attack is limited by the user's patience who usually does not tolerate more than 15 minutes without giving up the password. An Aircrack attack is limited by the power of the attacking machine; depending on the capacity of the machine, the search can take from days to weeks or even up to one month.
Depending on the management of the company, it is necessary to train the employees to identify the attacks on the networks, and thus avoid providing relevant information so the attacker can access the network. A mechanism to increase the security of entry to a private Wi-Fi network is the authentication through the devices Mac addresses. This mechanism not only allows the known devices to access, but also provide a degree of security.